Prefetch in Windows
Prefetch is a "tool" that I have used many times previously in different "forensic investigations", put simply, due to how simple it is to use, and how valuable it can be.
In case you are not familiar with it, Prefetch is a directory that you can access by navigating to C:\Windows\Prefetch or just typing "Prefetch" in RUN. It is a directory that is filled with Prefetch files (.pf) that are created when a program is run. You will notice that all the names match programs you may recognize on your system.
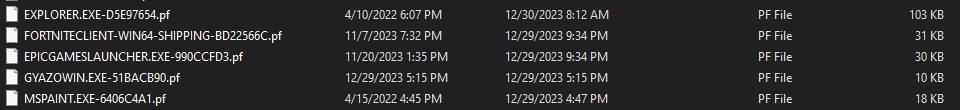
You can see when the programs were created and last run on the system.
This is just about where my knowledge used to end. I used Prefetch in forensic investigations in an attempt to gather evidence on players who were suspected to be using unfair modifications on our game servers. I would find the game application (javaw.exe) and when it was started, and then look for any suspicious-looking programs that were run afterward. Another positive of Prefetch was that even if the file was deleted, it would still show, which only gave even more suspicion.

If I found a suspicious program that I wanted to investigate further, this is where my time in Prefetch ended. I would go to a different program called LastActivityView to find out more details (little did I know at the time, LastActivityView uses Prefetch as one of its information sources).
I had to use this different program because I thought just the program title names and dates were the only useful aspects of Prefetch. This posed different problems because I couldn't see the app icons, or arguably most importantly, the directory file path of the specific program. That means individuals can simply rename their cheat execution file to something common like SVCHOST.EXE-... and it can be easily disregarded.
It wasn't until recently I started researching Prefetch more, where I found a diary by the Internet Storm Center (ISC) called "Forensic Value of Prefetch" https://isc.sans.edu/diary/Forensic+Value+of+Prefetch/29168
Through this diary, I was able to learn a ton about Prefetch.
Firstly, the "random numbers" after the file name is a hash of the directory where the file resides.
Secondly, the Prefetch files (.pf) store a lot more useful information than what is just visible from the outside. A program named PECmd created by Eric Zimmerman as mentioned in the diary can retrieve all the data from either a single Prefetch file or the entire directory. Here is the result I got by running the PECmd.exe:
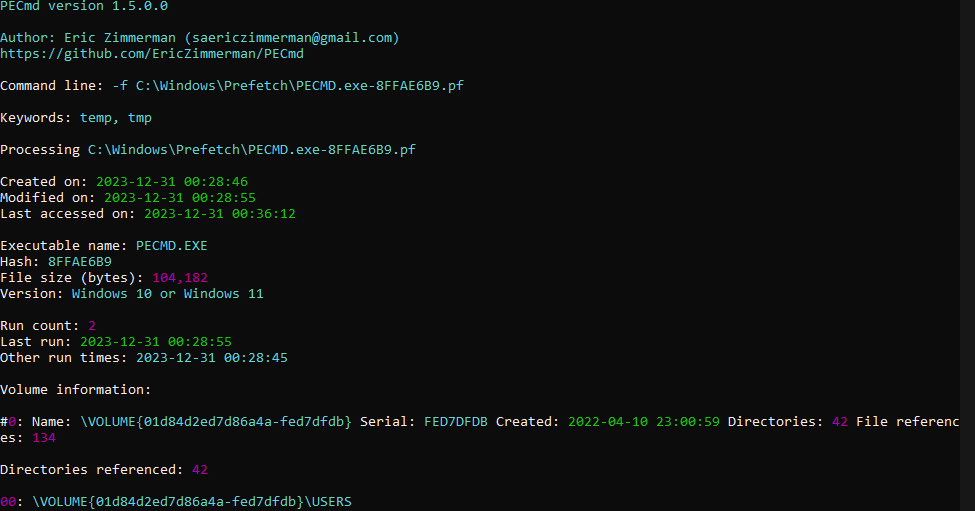
Pretty cool right? That isn't the entire output but it goes to show how much information is contained in the Prefetch files.
Here is a PECmd scan on a file that is known to be a cheat that a player would inject

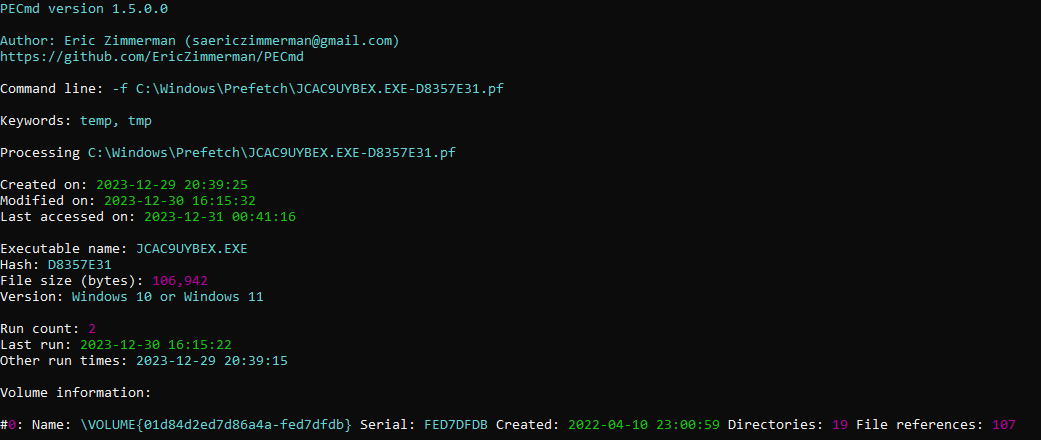
From the directories referenced, I would be able to trace back the location of the executable and verify whether the file was a cheat client or not.
If a novice like me was able to take advantage of Prefetch without even knowing its complete extent, I believe that goes to show how useful Prefetch can be in a forensic investigation, especially when paired with other sophisticated forensic tactics. I would like to thank the great ISC Diary by Johannes Ullrich which taught me this newfound information, and hope that this was able to give you an insight into a different perspective.