Hunting Encoded PowerShell Commands in Defender
In Microsoft Defender under "Advanced Hunting," I ran several different queries to see if I could find anything interesting in the environment. This was my first time experiencing the hunt capabilities, and I really enjoyed learning about how useful this is. One of these queries was to look for any activity surrounding encoded PowerShell commands, a common tactic used to obfuscate and deliver payloads.
The query that was run was this:
DeviceProcessEvents
| where FileName in~ ("powershell.exe", "pwsh.exe")
| where ProcessCommandLine has_any ("-enc", "-e ", "-EncodedCommand")
| project Timestamp, DeviceName, AccountName, FileName, ProcessCommandLine, InitiatingProcessFileName, InitiatingProcessCommandLine
| order by Timestamp desc
While sorting through the results, upd.exe stood out to me, which was out of the ordinary. I appended this filename to the query to narrow it down and find any instances, where I found about 30 results.
It had a Base-64-encoded payload, as you would expect from this query.
After decoding the payload, it revealed this:
$fn = [IO.Path]::GetRandomFileName().Split('.')[0] + ".txt"
"273572 --channel=1 --notify_api=https://searchsnfinds.com/ --token=***** -a" > "$env:TEMP\pdf\$fn"
This prepares a stager as a randomly generated file name is placed in the "pdf" folder inside the temp directory. I ran a search for the domain against VirusTotal and saw these results:
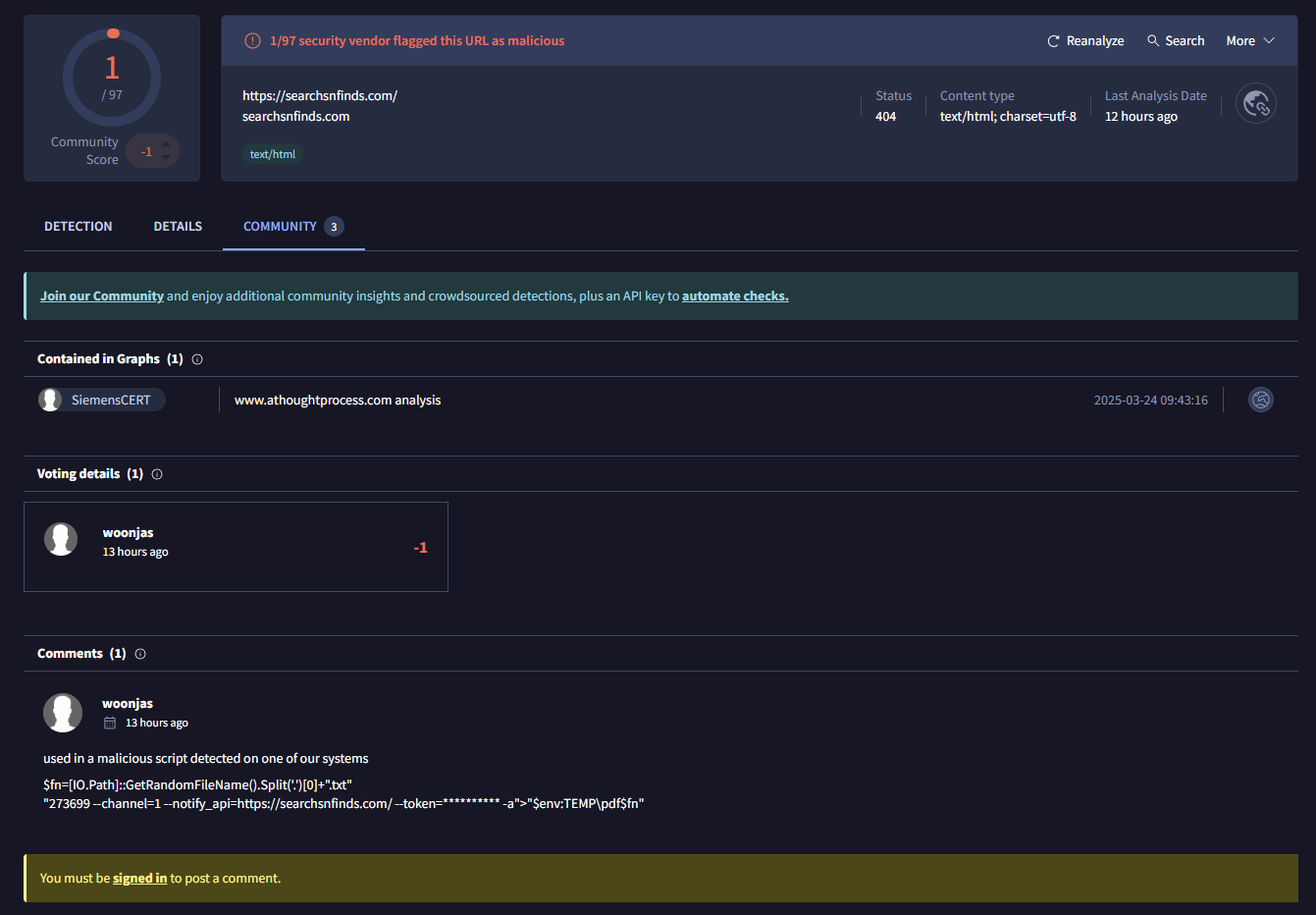
I ran another query to find more information surrounding the files:
DeviceFileEvents
| where FileName == "upd.exe"
| project Timestamp, DeviceName, SHA1, FolderPath, InitiatingProcessFileNameThis led me to finding more details surrounding the file, like its FolderPath, which was ...\AppData\Roaming\PDFast
Upon further investigation and research, I found some information regarding PDFast online. It looks to be freeware bundled with malware.
https://www.todyl.com/blog/threat-advisory-pdfast-freeware-compromise
https://www.joesandbox.com/analysis/1645050/0/html
I also found connections to a formerly resolved Defender for Endpoint incident where the files were detected as "Wacatac" malware.
Following the information I found in my hunt and online, I created a detection rule targeting all of the known malicious SHA256 hashes in DeviceProcessEvents.
For automated response actions, I choose:
- Full Defender AV scan
- Creation of an investigation
- Blocking of hashing across endpoints
This was my first hunt in Defender and custom detection rule, and I see the value this brings regarding threat hunting and investigations. Upon writing this, I think I will go back and see if I can also incorporate a check for that domain, if the tenant block list doesn't already prevent that.