Auditing M365 Mailbox Permissions
While reviewing the Identity and Access Management (IAM) lifecycle in SEC401, one concept that stood out to me was revocation. This step is often overlooked in the access management process. One area that I thought of immediately where revocation is frequently skipped is M365 mailbox permissions.
Where? Why?
In most organizations, it's normal for staff to be temporarily granted access to mailboxes, whether for onboarding, helpdesk requests, or part of an automation workflow. However, once the job or task is complete, that access is rarely cleaned up.
Permissions get added quickly, but they are not often tracked or removed. That becomes a problem, especially with shared mailboxes.
Bryan Simon, the author of SEC401, said something like, "Attackers don't know what access they have when they compromise an account." But do you?
Shared Mailboxes
Shared mailboxes usually contain a lot of critical communication. There are often inboxes like "HR@," "Support@," and "Finance@" where if a user still has access they no longer need or if an account gets compromised, that mailbox becomes an easy target.
Auditing user and shared mailbox permissions regularly can help spot over-privilege accounts and reduce risk. This is even more important as your environment grows and changes.
Quick Insights
One day at work, I quickly spun up a script to audit mailbox permissions in an environment and then revoke permissions. During the process, I thought it would be a great little project to create an all-in-one "mailbox audit tool" with multiple functions to make the audit process quick and easy.
I now created a PowerShell script (with help from technology) that audits mailbox permissions across Microsoft 365. It has three main functions:
- List all mailbox permissions across the tenant
- Get a complete overview of who has access to what, both user and shared mailboxes
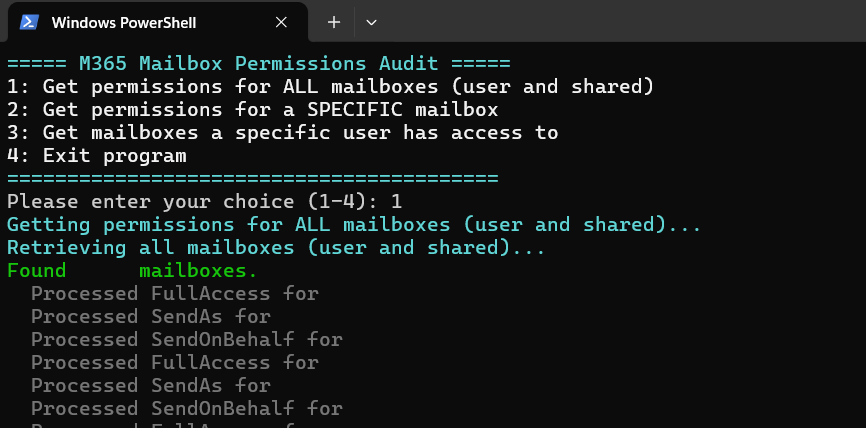
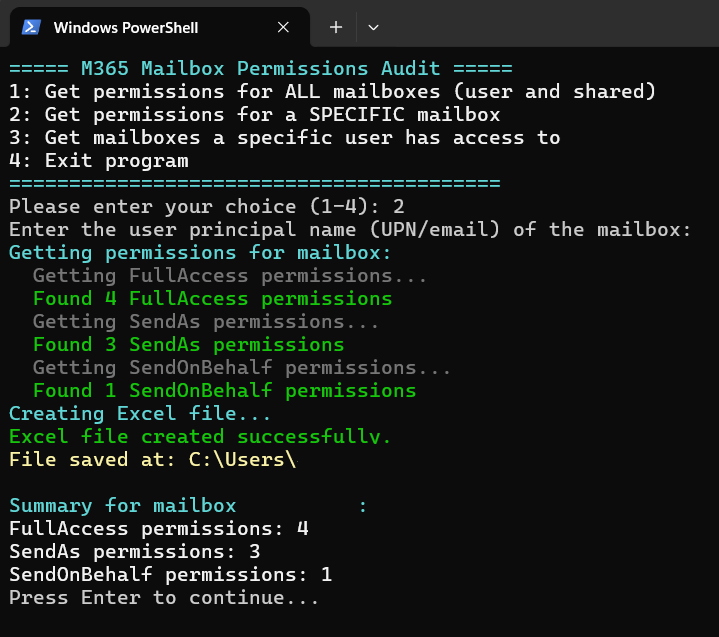
- List all users with access to a specific mailbox
- Useful for checking high-value or sensitive mailboxes.
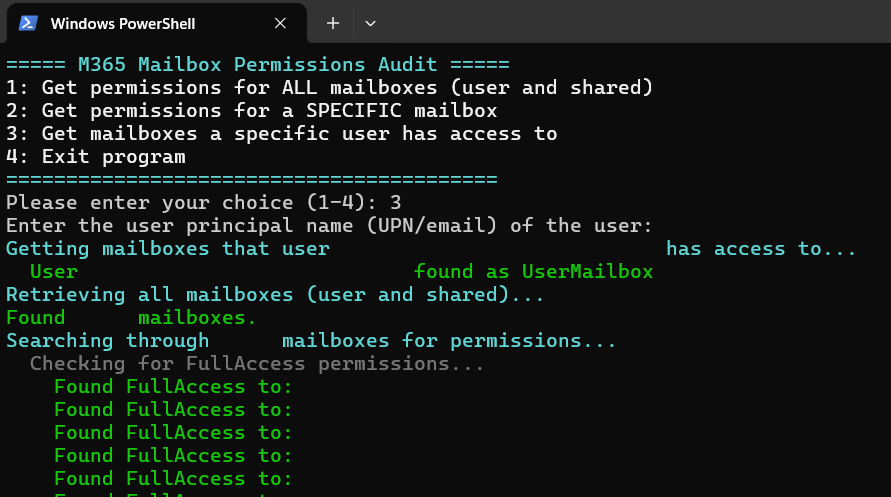
- List all mailboxes a particular user has access to
- Helpful for access reviews, offboarding, or role changes
Each output is saved in a clean, Excel-formatted table to simplify reviewing or reporting.
Before running any script, especially one that touches permissions, please read through it to understand what it is doing and test it in a safe environment. This one is focused on auditing only, with no changes made to mailbox access.
A link to the GitHub repository with the script can be found here:
Final Thoughts
I’m glad I could immediately apply concepts from my SANS program to a real-world scenario. Auditing mailbox permissions doesn’t have to be long or complicated; hopefully, this script makes the process a bit easier.
That being said, auditing is only the first step. It isn't very helpful if you don't follow through by reviewing the results and cleaning up what doesn't belong.
